CLOUD ENDPOINT DETECTION AND RESPONSE (EDR)
Cloud robust EDR security layer that continuously monitors endpoints for known and unknown threats and fully automates response workflows across the environment
98% OF ENTERPRISES HAVE CONTENDED WITH A CLOUD SECURITY BREACH IN THE LAST 18 MONTHS
Cloud Security is Business Assurance
Cloud is where your business operates, where it innovates, how it enables employees, and how it connects with customers. Adversaries know this, and that’s why attacks against cloud assets in IaaS, PaaS, and SaaS environments are increasing. With Reveal(x) 360, you can mitigate the blast radius of advanced threats like ransomware and supply chain attacks with unified security across multicloud and hybrid environments in a single management pane.
EDR provides comprehensive visibility and protection across all attack vectors, fully automating response workflows across the entire environment, all backed by a 24/7 MDR service
Advanced endpoint detection techniques to prevent and detect both known and unknown threats across your environment
Full visibility across endpoint, network and users, along with deception technology, to detect stealthy attacks
Automatically launch responses that chain various investigation and remediation actions into a single flow
cybersecurity experts monitor your environment 24/7 to ensure that no attacks are overlooked and provide expert advice and guidance
Go beyond EDR to XDR
Goes beyond traditional endpoint protection, combining telemetry from additional sources, to improve visibility, accuracy and protection across the entire attack surface.
-
Next-Gen Antivirus
Blocks execution of malware, exploits, fileless, Macros and ransomware
-
Network Detection and Response
Monitor network traffic to unveil reconnaissance, credential theft, lateral movement, and data exfiltration attempts
-
User Behavior Analytics
Profile the behavior of all user accounts to pinpoint anomalies that indicate an attempted compromise
-
Deception Technology
Plant various types of decoy files across your environment to lure attackers into revealing their presence
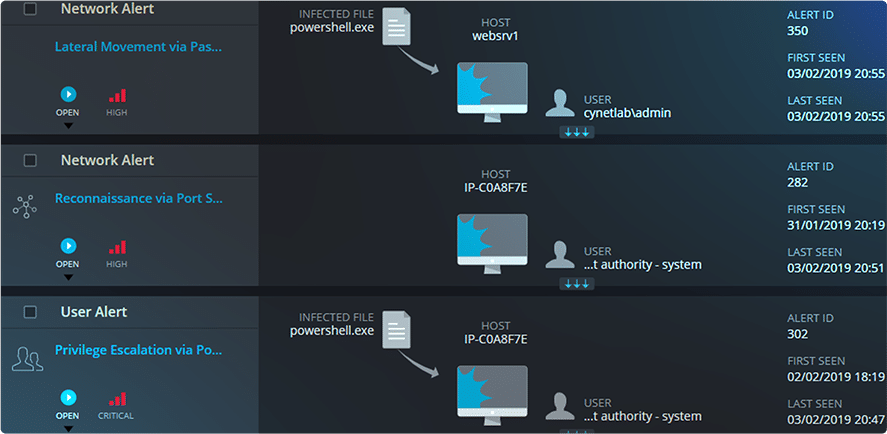

Unify incidents
Cynet automates investigations by combining related alerts into unified incidents.
End-to-end Response
Single, unified view eliminates the need to switch between solutions for investigation
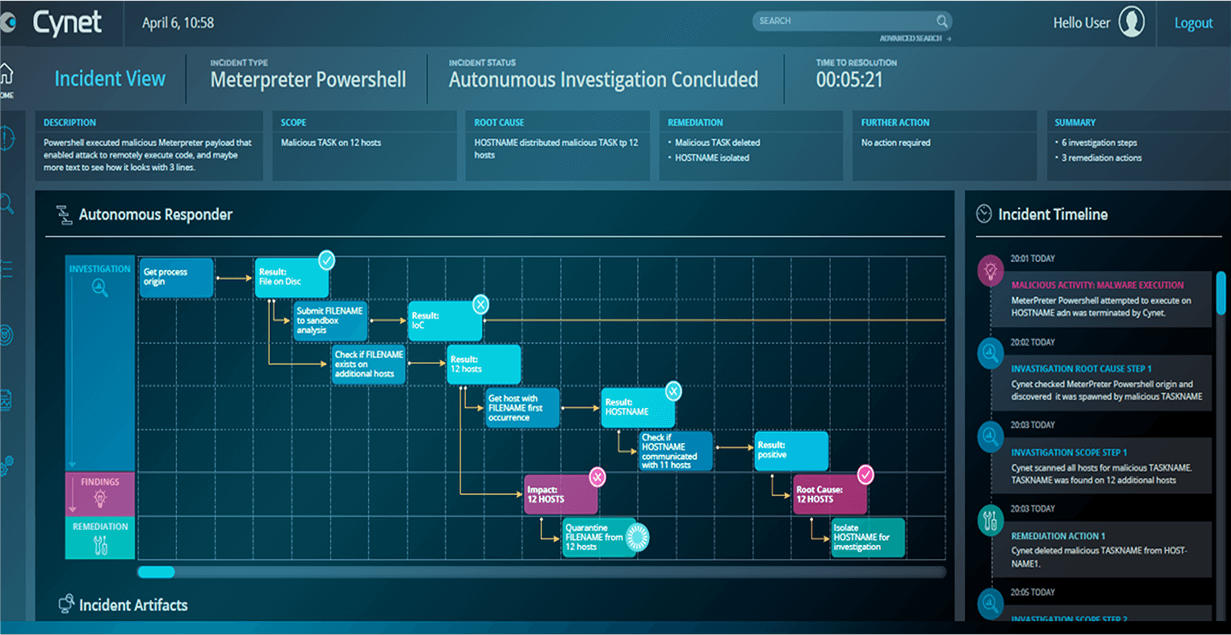
Incident View
Correlate signals from multiple native detection sources into incidents to visualize and understand threat context
- Automated Response
IOCs
Uncover Indicators of Compromise (IOCs) and anomalous behaviors
Simplify investigations with automated root cause analysis and full threat scope visualization